Real-time Dashboards
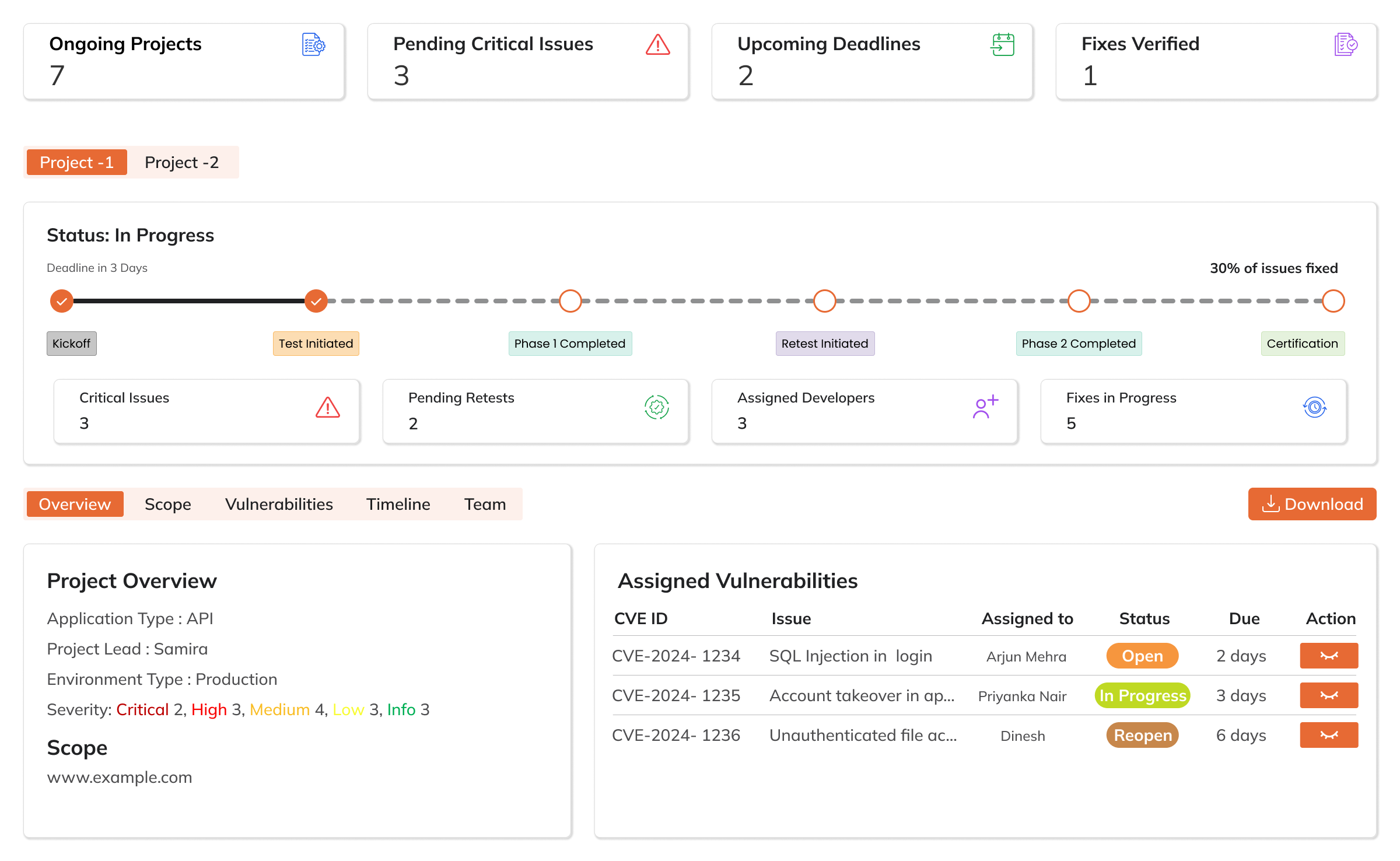
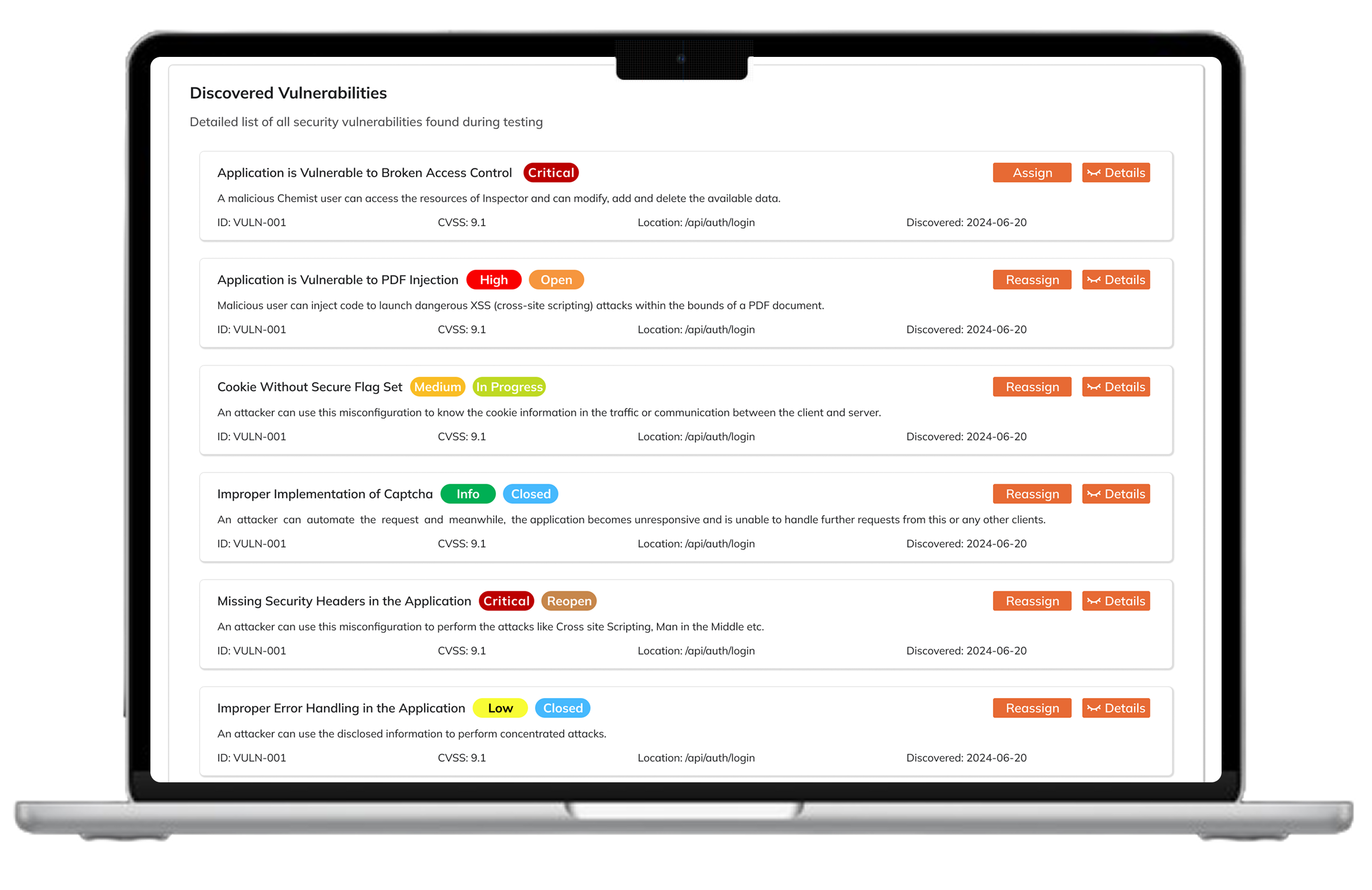
Track, triage, and remediate vulnerabilities seamlessly with customizable workflows, RBAC, and real-time dashboards.
Security teams often juggle multiple tools, endless email threads, and scattered spreadsheets just to keep track of vulnerabilities, pentest findings, and remediation progress. This fragmented approach slows down response times and increases the risk of missed critical issues.
Your command center to track, triage, and remediate faster—bringing pentest, bug bounty, and scanner findings together with customizable workflows, RBAC, and real‑time dashboards.
Consolidate findings, automate workflows, and gain full visibility into remediation progress—all in one place.
Define stages, severities, and SLAs to match your process—from initial triage to final verification.
Fine-grained permissions ensure only authorized users can view, edit, or assign vulnerabilities.
Aggregate pen test, bug bounty, and scanner findings into a single, organized workspace.
Track backlog, SLA breaches, and ownership at a glance with live project & vulnerability views.
Assign owners, sync status, and keep fixes moving with comments, mentions, and audit logs.
Verify remediations quickly with repeatable checks and clear pass/fail evidence.
Ingest pentest, bug bounty, and scanner findings into one queue with deduplication.
Prioritize by severity, asset value, and SLAs with clear ownership assigned to each vulnerability.
Track fixes, validate remediations, and close issues with automated retest cycles.
See how your projects and vulnerabilities appear in real-time dashboards. Map your workflows, import sample findings, and discover how quickly your team can gain control.
No credit card required. See value in minutes.


