Vulnerability Assessment and Penetration Testing

What is VAPT?
Vulnerability Assessment & Penetration Testing (VAPT) is a comprehensive cybersecurity approach that helps organizations identify, exploit, and remediate vulnerabilities across applications, networks, cloud platforms, and infrastructure.
At ISECURION - a CERT-In empanelled provider - we deliver advanced VAPT services combining automated scanning, expert-led manual testing, and compliance-focused reporting for ISO 27001, SOC 2, PCI DSS, HIPAA, and RBI guidelines.
Key Benefits of VAPT
Security incidents cause data breaches, reputational harm, legal exposure, and business disruption. VAPT helps organizations identify weaknesses before attackers exploit them, ensuring a resilient security posture.
Prevent Breaches
Proactively detect and remediate high-risk vulnerabilities before exploitation.
Stay Compliant
Align with ISO 27001, SOC 2, PCI DSS, HIPAA, and RBI mandates effortlessly.
Build Trust
Provide security assurance to customers, regulators, and stakeholders.
Incident Readiness
Improve detection, response, and recovery capabilities.
Reduce Costs
Prevent financial losses from downtime, penalties, and breach recovery.
Stronger Security
Identify attack surface and strengthen defenses continuously.
Our Proven VAPT Methodology
We follow globally recognized frameworks like OWASP, NIST, PTES to ensure high-quality, repeatable results. Our methodology not only strengthens cyber defenses but also supports compliance with standards like ISO 27001, SOC 2 Compliance, and Data Localization.
1. Planning & Reconnaissance
We define scope, rules of engagement, and gather OSINT for better context. This step aligns with compliance-driven scoping in UIDAI Aadhaar Audits and IRDA Guidelines.
2. Vulnerability Assessment
Automated + manual checks for CVEs, patch gaps, and insecure services. Findings help enterprises prepare for GDPR Audits and CSCRF (SEBI) Audits.
3. Exploitation
Ethical hacking to validate risks via proof-of-concept exploitation, ensuring real-world security posture improvements for VAPT Services across cloud, web, and mobile environments.
4. Reporting & Remediation
We deliver detailed risk ratings, compliance mapping, and re-test verification. Our reports are audit-ready and support frameworks like SOC 2 Compliance and ISO 27001.
Visual Representation of Our Process
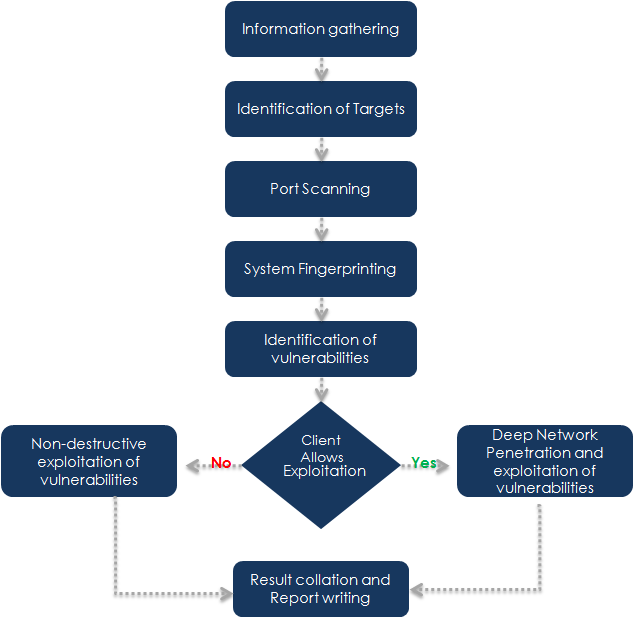
VAPT – Frequently Asked Questions
VAPT combines vulnerability assessment (finding known weaknesses) and penetration testing (safely exploiting them) to measure real risk and help you remediate issues across applications, networks, cloud and infrastructure.
It supports CERT-In advisories and sectoral guidance (e.g., RBI) while protecting sensitive data and brand reputation. Regular VAPT reduces breach likelihood and strengthens compliance posture (ISO 27001, SOC 2, PCI DSS, HIPAA, etc.).
At least annually, and additionally after major releases, infrastructure changes, new integrations, or whenever required by your compliance framework or client contracts.
Yes—these standards require vulnerability management and periodic penetration testing to demonstrate due diligence and continuous improvement.
We use safe, non-intrusive methods on production with change-control and rollback plans. For aggressive scenarios, we prefer staging environments with your approval.
A single web app or network segment usually takes 3–7 business days depending on complexity, integrations, and test depth.
You get an executive summary, detailed technical report with PoCs and evidence, risk ratings, remediation steps, and a closure/re-test report once fixes are validated.
A vulnerability assessment identifies weaknesses at scale; penetration testing confirms exploitability and demonstrates real impact. Together, VAPT provides both breadth and depth.
Yes. A re-test is included within the agreed window to verify fixes. Upon closure, we can issue an attestation/closure letter for auditors or customers.
Scope (targets, environments, tech stack), access method (black/grey/white-box), test window & change-freeze, contact points, and any compliance requirements to map in reporting.
Request a Free VAPT Consultation